We (my wife Lisa and I) have finally completed the South Downs Way on Friday 16th July having originally commenced it on 25th May 2019! My knees may never recover as The Seven Sisters took their toll.
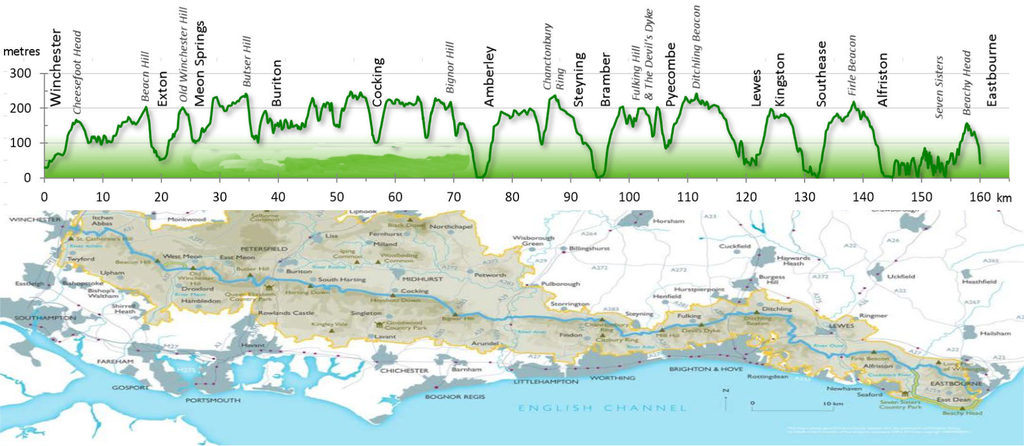
The map and elevation guides above show the route from Winchester in Hampshire, England through to Eastbourne in Sussex. During the walk we gained one dog, several pounds in weight and two years in age including one with a zero for me. We lost the year of planning to complete the route in 2020 due to the global pandemic.
Many will do the walk faster or complete tougher/longer walks. We have done tougher individual climbs Helvellyn in the Lake District a notable previous trip.
I’ve created a full gallery page which you can find here with all the photos and more than are in this blog. The scenery is stunning, the natural world and wildlife is wonderful. It’s not as exotic as Borneo or Costa Rica but a lot closer to home. For the quintessential England of rolling hills, and patchwork colours, it’s hard to beat.
Using the excellent pocket guide, South Downs Way by Jim Manthorpe & Daniel McCrohan which helpfully splits the route into legs travelling West to East. The reverse is also available for those wanting to travel East to West.

We started off in May 2019 with the aim to complete that summer but as usual life got in the way and we had only completed 70 of the 100 miles from Winchester by the end of November 2019. We drove away from Pyecombe on a bright but cold early winter’s day when the short daylight hours limited further attempts. We stopped for the winter expecting to restart in Spring 2020. Well nothing restarted until July 2021. We managed to book some accommodation for now two dogs and two adults. Not easy at best of times as few hotels, B&Bs or cottages are available that take dogs and cottages. (They wanted a lot of money and a week’s booking too.)
The walk is full of stunning views and panoramas:


In November 2019, we had managed two days in a row with calm weather even if cold and despite arriving in the dark. Going downhill at dusk can be fun – not. We split two days walking with a stay in the South Downs Way B&B Poynings (Very Good). The B&B lies in the valley off of the walk and therefore not at a start or end point.

Previous days we had driven to the day’s end point then taken a taxi (dogs allowed booking) back to the start point. On one day, for Leg 4, we had taken the train from Amberley Station to Chichester, and then a bus to a start point in the lay by ending from Leg 3. These were new experiences for Merlot our then 9 year old lone tricolour border collie, since joined by his great nephew Malbec. Both MastaMariners

Leaving the car in a lay bys or car parks to be reclaimed with tired and muddy walkers and one dog at that time, is fine if the journey back home is about an hour. As we ventured further east the trip out and back increased, traffic and weary bones starts limiting the enjoyment so more planning for overnight stays and therefore hopes of good weather.
We were lucky on nearly every occasion. On only one day did we have heavy rain at any point and that was on Leg 2 when despite a reasonable forecast our luck did not hold.
Then again there were days with glorious weather, too warm to walk and the problem of water. The heat of summer did lead to some spectacular sights.

There were occasional unexpected stops


Finally in July 2021 we were able to re-start and complete the walk. Two nights staying in the centre of Lewes (pronounced Lew-is) at The White Hart (Needs some TLC). This covered Leg 7 – which was a long leg. Some great views but one very long concrete paved track down hill into Southease followed by a train back into Lewes. Even Malbec making his debut was not impressed.

We ate local meals in the centre with an accompanying local beverage. The beer had to travel across the road!

This was followed by two nights in Eastbourne at the York Hotel on the sea front (nice with a pool and a sea view in a large room!). The legs had fabulous scenery and increasing temperatures.
There is a choice for walkers for the last leg, inland or down to the coast. We chose the coastal route. The leg was tough going covering the walk to the coast from Alfriston, past the Litlington White Horse (across the valley) through to Seven Sisters Country Park and then the Seven Sisters themselves and Beachy Head. A lot of up and down in a roller coaster path, for which the ticket entry was painful knees and more blisters.






Finally a suitable toast with my beautiful wife to complete the walk

Legs
Leg 1 – Winchester (elevation 20 feet at Riverside) to Exton – 25th May 2019 – 12 Miles / 19.5 km – two main climbs Cheesefoot Hill 577ft and Beacon Hill 659ft
Leg 2 – Exton to Buriton (Queen Elizabeth Country Park) – 15th June 2019 -12.5 miles / 20 km – Butser Hill 886 ft
Leg 3 – Buriton to Cocking – 16th July 2019 10.5 miles / 17 km – Beacon Hill 794 ft
Leg 4 – Cocking to Amberley – 3rd August 2019 – 11.5 miles / 18.5 km – Bignor Hill 738 ft
Leg 5 – Amberley to Steyning – 28th November 2019 – 10 miles / 16 km – Chanctonbury Ring 771 ft
Leg 6 – Steyning to Pyecombe – 29th November 2019 – 10 miles / 16 km – Devils Dyke 673 ft
A long break….
Leg 7 – Pyecombe to Southease – 14th July 2021 – 14.5 miles / 23.5 km – Ditchling Beacon 814 ft
Leg 8 – Southease to Alfriston – 15th July 2021 – 7.75 miles/ 12.5 km – Firle Beacon 712 ft
Leg 9 – Alfriston to Eastbourne (Meads) Coastal route – 16th July 2021 – 10.5 miles / 17 km – Beachy Head 538 ft